
Knowing how to recognize spear phishing vs phishing can prevent major financial losses.
All phishing emails aren’t created equal. Some are broad and obvious, meant to cast a wide net. Others are crafted with precision—targeting specific people, businesses, or even ongoing conversations.
Understanding the difference between phishing, spear phishing, and Business Email Compromise (BEC) isn’t just helpful—it’s essential. These threats all come through your inbox, but they use different tactics, target different people, and require different levels of awareness to stop.
If you’ve ever wondered about spear phishing vs phishing, or how BEC fits in, this blog breaks it down—plain and simple.
What Is Phishing?
Phishing is a type of cyberattack that uses fake emails, messages, or websites to trick someone into revealing sensitive information—like passwords, credit card numbers, or login credentials.
These attacks are usually broad and not personalized. They’re designed to reach as many people as possible in hopes that a few will take the bait. You’ve probably seen them: a fake bank alert, a suspicious package delivery notice, or a message asking you to reset your password.
Phishing attacks often include:
-
Generic greetings like “Dear Customer”
-
Links to spoofed websites
-
Fake login pages
-
Attachments disguised as invoices or documents
Because phishing is so common, many people are on alert for the red flags. But attackers have evolved—and that’s where spear phishing comes in.
💡 Did You Know?
A recent Verizon Data Breach report found that spear phishing emails have a 3x higher success rate than generic phishing, highlighting why knowing the difference between spear phishing vs phishing is critical for employee training.
What Is Spear Phishing?
Spear phishing is a more targeted, personalized version of phishing. Instead of sending a mass email, the attacker researches the victim and crafts a message specifically for them.
They might reference:
-
Your name and job title
-
Projects you’re working on
-
Your coworkers or clients
-
Internal terminology or tools your company uses
Spear phishing emails are harder to spot because they feel familiar. The attacker might pretend to be your manager, a client, or even your IT provider. The message may sound urgent, polite, or totally routine—because it’s designed to lower your guard.
If you’ve ever clicked something because it seemed just real enough, that’s the power of spear phishing.
💡 Did You Know?
According to the FBI, spear phishing attacks cost U.S. businesses over $2.7 billion in reported losses each year—and the real number is likely even higher.
What Is Business Email Compromise (BEC)?
Business Email Compromise, or BEC, is a type of spear phishing—but with higher stakes and a narrower target. BEC attacks focus on financial gain and often target executives, accounting staff, or others with access to money or sensitive data.
In a BEC attack, the attacker may:
-
Impersonate a CEO asking for a wire transfer
-
Pose as a vendor requesting updated payment details
-
Hijack a real email thread to inject fraudulent instructions
These emails are usually well-written, timely, and part of a bigger strategy. The goal is often to divert funds, steal sensitive information, or exploit trust inside your company.
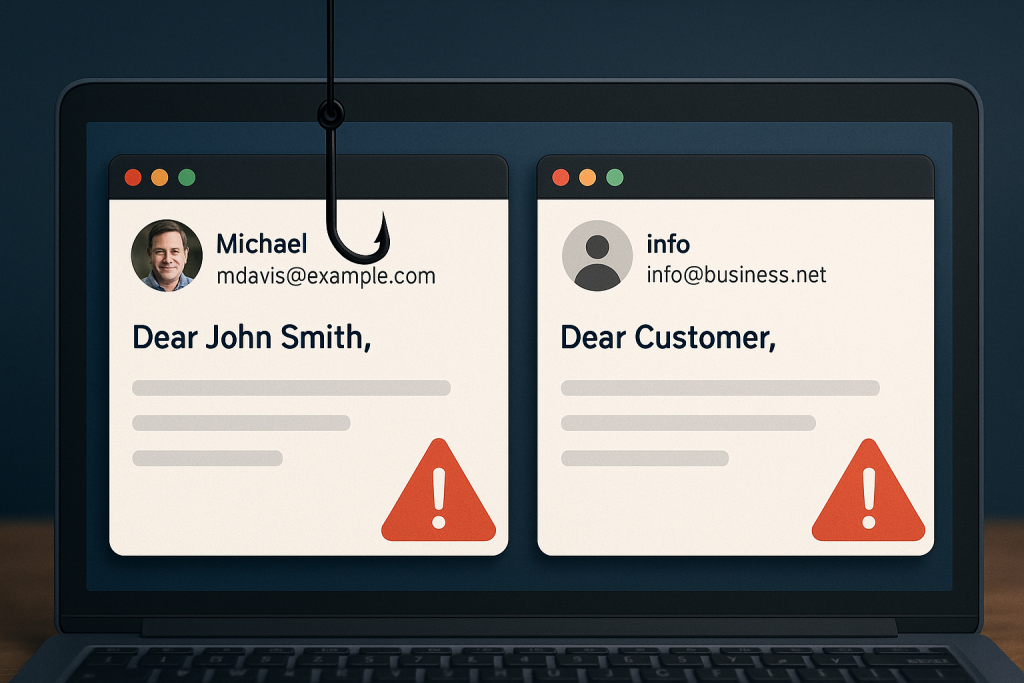
Spear phishing vs phishing: Learn the key differences and how each attack works.
Spear Phishing vs Phishing: What’s the Real Difference?
The key difference between spear phishing vs phishing is personalization. Phishing casts a wide net. Spear phishing zooms in on one target. Both are dangerous, but spear phishing is more likely to succeed—especially when the victim doesn’t know they’re being targeted.
Phishing = generic
Spear phishing = specific
BEC = financial or executive-level spear phishing
Think of them as levels on a scale—from low-effort scams to sophisticated, researched attacks.
💡 Did You Know?
Nearly 90% of BEC attacks begin with a spear phishing email—making it one of the most financially devastating threats businesses face.
Real Example: Phishing vs Spear Phishing vs BEC
Phishing:
An email says your Netflix account has been suspended. It includes a link to “update your payment method.” The email is generic and sent to thousands of people.
Spear Phishing:
An attacker sends a message to your HR manager pretending to be a new applicant. The resume attachment contains malware that gives them access to your system.
BEC:
Your controller receives an urgent request from the “CEO” asking to wire funds to a vendor to close a deal. The email looks legitimate and mimics the CEO’s style.
All three are dangerous. But only one targets your team, your business, and your money directly.
How to Protect Against All Three
Stopping phishing starts with awareness—but protection means layering the right tools and training together.
At Professional Computer Concepts, we help businesses reduce risk from phishing, spear phishing, and BEC through:
You don’t need to be a cybersecurity expert. You just need the right partner—and the right plan.
💡 Did You Know?
Understanding the difference between spear phishing vs phishing can significantly improve incident response—because each attack type targets different people, data, and decision points.
Want to Go Deeper?
If you’re looking to train your team or better understand phishing from all angles, these resources are a great place to start:
- How to Spot a Phishing Email: 10 Red Flags to Watch For
- Real Phishing Examples: Recognize Email Scams Before You Click
- Ultimate Guide to Phishing + Quiz
- Lookalike Domains: How Hackers Trick the Eye
- The Danger Behind Display Names: Email Spoofing Explained
- Attachment Red Flags: When Not to Open That PDF
- How to Prevent Phishing Attacks
- Phishing: What You Need to Know
- Phishing 2.0: The Rise of AI-Driven Attacks – Defend Yourself Now
Final Thoughts
Phishing, spear phishing, and BEC attacks may look different on the surface—but they all start with the same thing: an email that’s trying to get past your instincts.
Knowing the difference between spear phishing vs phishing helps your team respond more effectively. It helps your leaders take the right precautions. And it helps you invest in the kind of cybersecurity that works—not just in theory, but in practice.
Let’s talk about making your business harder to scam—and easier to protect.

